introduction
We have collated all the most Frequently Asked Questions with regards to Application & Operational Security, Architecture and Development, Permissions and Authentication, Data Handlings Security & Privacy and Business Continuity.
If you still have any questions please do not hesitate to contact us: trust@ennova.com
Contents
Application & Operational Security
Architecture & Development
Permissions & Authentication
Data Handling Security & Privacy
Business Continuity
Uptime
You can access our Security Portal via the following link: https://securityportal.ennova.com/
Here you can find and download important security information – including documents, reports and certificates.
Application & Operational Security
Ennova strives to follow Microsoft 365 best practices for the Operational Security / Secure Application Deployment security domain. To support us in this we have teamed up with Fellowmind whom supports and operates our infrastructure.
Secure Development Lifecycle (SDLC)
Secure Code Education
In order to ensure proper knowledge and training Ennova utilizes Pluralsight to ensure that developers has the proper knowledge of OWASP Top 10 security risks, common attack vectors, and Azure security controls.
Framework Security Controls
Ennova utilizes the Microsoft .Net platform that includes both ASP.NET, .NET Core, Angular and modern and secure open-source frameworks with security controls in place to limit exposure to OWASP Top 10 security risks. These inherent controls reduce our exposure to SQL Injection (SQLi), Cross-Site Scripting (XSS), and Cross-Site Request Forgery (CSRF), among others.
Quality Assurance
Our developers review and tests the codebase for every change implemented. Business partners helps with internal end user testing.
Separate Environments
Development, Testing, Quality Assurance environments are logically separated from the Production environment. For a very few cases Anonymized customer data can be used for testing purposes after following a rigid and automated anonymization process.
Penetration Testing
3rd-Party Penetration Testing
The Penetration Testing for Ennova is conducted at least annually by Dubex, an independent company based in Denmark.
The Pen Test is limited to the Ennova Platform and should be read in conjunction with the Penetration testing on Azure carried out by Microsoft on the Azure platform. The test gives valuable insight to help improve the platform and guides actions in terms of improving security controls, introducing new security controls, and improving our security processes.
Vulnerability testing
Every other month a vulnerability test is performed by Dubex, an independent company based in Denmark.
Ennova does also perform vulnerability testing of own code using Burp Suite Professional.
This helps improve the platform and guides actions in terms of improving security controls, introducing new security controls, and improving our security processes in adjunction to the Penetration test.
Advanced Platform Security & Threat Protection
To secure the Ennova platform and protect our customers' data from intrusions we make extensive use of the latest Microsoft 365 & Azure security technologies & services, including:
- Network Security/Firewall - All Azure resources can communicate with each other privately, through private IP addresses. Azure network security groups are used to filter network traffic to and from the Azure resources in an Azure virtual network.
- Azure DDoS Protection - All Azure services and VNets used in the Ennova Platform architecture are protected against Distributed denial of service (DDoS) attacks.
- Auditing for SQL Database is enabled on all production Azure Servers and databases and audit logs are stored for a minimum of 1 year.
- Azure Key Vault a cloud service for securely storing and accessing secrets, tokens, certificate storage, and management. In addition to this they can also be stores in variable sets encrypted in the deployment system
- Azure Defender for Azure SQL database servers include functionality for identifying and mitigating potential database vulnerabilities and detecting anomalous activities that could indicate threats to your databases
- Azure Defender for Cloud includes functionality to continuously Access, Secure and Defend azure resources such as servers and storage
- All staff operating and supporting the Ennova Platform are working on Compliant Windows 10 devices managed using Microsoft Endpoint Manager (Microsoft Intune) including Microsoft Defender anti-virus and firewall and supplemented by Heimdal™ Threat Prevention.
Architecture & Development
Platforms and Standards
The Ennova Platform is developed to run natively on the Microsoft Office 365 and Azure platforms and follows all of Microsoft recommended practices about Design and Development of the solution.
Many of the questions we receive are applicable to the platform on which the Ennova Platform is deployed and we have created a shortlist of the most commonly requested standards and whether the platform is compliant with these standards.
For Ennova as a company the following applies:
| Standard | Compliant |
| ISO/IEC 27001:2013 Information Security Management Standards | Yes |
| SOC2 Type 2 | Yes |
For the Microsoft Office 365 and Azure Platform the following applies:
Microsoft Trust Center
Many of the questions we receive are related to the platform we run on. All platform questions can be answered by visiting the Microsoft Trust Center.
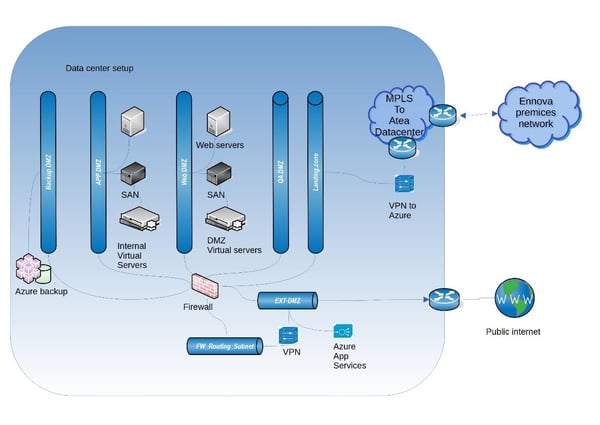
Ennova Infrastructure overview
This diagram below shows the architectural setup of the infrastructure.
Permissions & Authentication
Authentication
Internal Users
Enova utilizes the Office 365 and Microsoft 365 identity models offered by Azure Active Directory and Active Directory for all users and authentication. For more information follow this link.
External Users
Ennova can utilizes Azure Active Directory or OpenId Connect for all External Users on the Platform. For more information follow this link.
Multi-factor authentication (MFA)
To increase security Ennova supports MFA if Single Sign On is used, and can be enabled without any issues on the customer side. For more information about setting up MFA for your Office 365 Tenant follow this link.
Data Handling Security & Privacy
How Ennova Keeps your Data Protected
Some of the steps we have taken in dedication to this data security intention include:
- Backup and disaster recovery
- Ability to ensure ongoing confidentiality, integrity, availability, and resilience of the IT infrastructure and environment
- Information Security Awareness training program for all staff
- Regular testing and evaluation of the effectiveness of our measures including both internal and external audits.
Additionally, Ennova commits to only partnering with subprocessors that operate in accordance with GDPR regulations and standards of data protection. All subprocessors have to pass a predefined selection process, based on a company policy.
Personal Data & Data Storage
Data Storage
All customer data is logically separated in systems and databases. Automated and manual tests are conducted upon every change to the system to ensure segregation of data.
Content Storage
Content shared between the customer and Ennova is stored on a fileserver or Office 365 service only accessible to the team handling the customer.
Different Azure storage types can be used depending on the product.
Technical Support Telemetry
To improve technical support investigations, we track requests done at the Ennova Platform using Microsoft Azure Application Insights and Splunk Logging. In the requests we register the amount of data needed to support our customers. An example could be:
- User Login Name (i.e. Email Address)
- Name
Microsoft Azure Application Insight data is secured and is only kept for 90 days and is then deleted automatically by Microsoft.
Splunk data is stored for 3 years and after that automatically deleted by the system.
Data Security and Encryption
Ennova use end-to-end Encryption as a security measures to protect customer data being processed while data is both in transit and at rest.
Data in Transit
Transmission of data between the application and Azure is secured using an encrypted TLS 1.2+ connection with AES encryption. SSL/TLS certificates are signed by a publicly known Certificate Authority using the SHA256 with a 2048 bit key.
Cookies containing session information and other sensitive data from the Ennova platform are all configured with HttpOnly and Secure flags enabled. This protects the cookie contents from being accessed by scripting as well as from being transmitted over unencrypted connections.
Data at Rest
Storage data
Data in Azure Storage is encrypted and decrypted transparently using 256-bit AES encryption, one of the strongest block ciphers available, and is FIPS 140-2 compliant. All Azure Storage resources are encrypted, including blobs, disks, files, queues, and tables. All object metadata is also encrypted.
For further information please visit: https://docs.microsoft.com/en-us/azure/storage/common/storage-service-encryption
Azure VPN encryption
Accessing customer data on the Ennova platform requires a Point-to-site VPN connection using GlobalProtect and a certificate with a 2048 bit RSA Encryption key to creating a secure tunnel with the Azure AD authorization to protect the privacy of the data being sent across the network. The Azure VPN client is distributed through Intune and is available for installation only by authorized users.
Ennova endpoint
All Ennova equipment used by employees is encrypted at the endpoint. This includes computers, phones and any attachable devices.
Access to Customer Data
Customers Access to their Data
Customers can get access to the data through the Ennova Platform where a role and permission scheme is in place to ensure the right roles and permissions.
2nd Party Access to Data
Under normal operational circumstances, Ennova IT and Support Staff will never access the customer's data.
Ennova IT will from time to time require access to the Customer’s Data when investigating an issue reported by the customer.
Access to all production systems is always controlled and supervised by our IT Operations Team and only allowed from a compliant company-managed device from protected IP ranges.
All staff has signed our Confidentiality Agreement.
To administrate privileged access, organizational structures are in place to govern who is granted access to what in accordance with our Information Security Policy.
Microsoft Access to Data
Ensuring security in the processing of customer data stored and shared via the Microsoft Cloud is critical to Microsoft. Read more about how Microsoft handles data in the cloud on https://www.microsoft.com/en/trust-center/privacy/data-access
Data Breach Detection & Notification
All our services and personnel follow internal incident management procedures to ensure that we take proper precautions to avoid data breaches in the first place. However, in addition, Ennova, Fellowmind & the Microsoft Azure cloud services have specific security controls in place across our platforms to detect data breaches in the rare event that they occur.
In the event of a breach, i.e. a breach of security leading to accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, Personal Data transmitted, stored, or otherwise processed, Ennova will without undue delay notify the Data Controller in writing and additionally in any other reasonable and prompt manner (e.g. by phone or email).
In the event of a security breach, our team will promptly notify the customer of unauthorized access to their data.
The Breach notification will contain at least the following:
- Nature of the personal data breach (categories and approximate number of datasubjects concerned and the categories and approximate number of personal data records concerned.
- Name of contact point at Ennova.
- Description of likely consequences of data breach.
- Description of measures taken or proposed to be taken by the controller to address the personal data breach
In some cases it will not be possible to provide the information at the same time, but then the information may be provided in phases without undue further delay.
Ennova takes all the necessary steps to protect the Data after having become aware of the Breach. After having notified the Customer in accordance with the above, Ennova will, in consultation with the Customer, take appropriate measures to secure the data and limit any possible detrimental effect to the Data Subjects.
Ennova will cooperate with the Customer, and with any third parties designated by the Customer, to respond to the Breach. The objective of the Breach response will be to restore the confidentiality, integrity, and availability of the Services, to establish root causes and remediation steps, to preserve evidence, and to mitigate any damage caused to Data Subjects or the Customer.
Business Continuity
Data Center Locations & Physical Security
The Ennova Platform is built entirely using Azure Services all operated securely in the Microsoft Azure cloud fully managed by Fellowmind and Ennova. All data is placed at the Azure datacenter West Europe (Netherlands).
Azure Facilities, premises, and physical security
Ennova doesn't have any in-house data centers, physical networks, and/or servers connected to the Ennova platform. Microsoft manages the physical and environmental security of our Azure-based data centers and the Azure physical security is described here.
Our internal security program covers physical security at our offices.
Data Backup, Retention & Media Sanitation
Ennova stores all data securely with full redundancy on Microsoft Azure. All data is backed up and backups encrypted with Transparent data encryption (TDE)
All database backups are managed automatically by Microsoft Azure and are backed up as follows:
| Full Backups | Daily |
| Differential | Every few hours |
| Transaction log | Every 5-10 minutes |
| Retention |
Monthly |
For further information please visit https://docs.microsoft.com/en-us/azure/sql-database/sql-database-automated-backups
Data Deletion & Media Sanitation
What happens to your data if you leave the service?
It is Ennova’ responsibility to permanently destroy the Customer Data upon Customer’s request, with special emphasis on destroying all data in the scope in all locations and ensure all copies have been discarded.
Ennova shall at its own discretion determine data destruction schedules but shall wherever possible perform such destruction in accordance with the Customers' requested timetable. Supplier shall have the obligation to wipe persistent media used for storing Customers Data or secure deletion of Customers Data with related techniques before it is released into re-use.
Data deletion & retention period
When the Ennova Platform subscription ends, Customer Data will be deleted according to the agreed time from the Ennova Azure Subscription. The data will still be available on the backup in accordance with the backup scheme after which time the data will be completely unobtainable.
Data deletion on physical storage devices on Azure
Due to Ennova being built on Microsoft Azure as a Software as a Service solution, Ennova doesn’t have physical access to wipe and destroy media used for storing Customer Data on Azure which follows Microsoft Media Sanitation guidelines below:
If a disk drive used for storage suffers a hardware failure, it is securely erased or destroyed before Microsoft returns it to the manufacturer for replacement or repair. The data on the drive is completely overwritten to ensure the data cannot be recovered by any means.
When such devices are decommissioned, they are purged or destroyed according to NIST 800-88 Guidelines for Media Sanitation.
Microsoft is governed by strict standards and removes cloud customer data from systems under our control, overwriting storage resources before reuse, and purging or destroying decommissioned hardware.
uptime
At Ennova we strive to deliver the best possible uptime for all our solutions with a minimum of 99,70 %.
Click on the link to see uptime for the last 12 months.

